Viewing posts tagged Authentication Attacks
Latest release pushes into Privileged Access Management
Posted by: admin 10 years, 2 months ago
The 4.1 release of the WiKID Strong Authentication Server - Enterprise Edition includes the ability to use one-time passcodes for Active Directory accounts. We noted an increasing focus on privileged accounts. Companies need these accounts to manage windows PCs and infrastructure. Multiple system admins need to have the credentials for them too. So, organizations often have shared spreadsheets with credentials. You can put them into a "password vault" but then there is still a password to the vault and an attacker that is already on the system can still perform a 'pass-the-hash' attack to escalate their privilege.
Yet another reason to add two-factor authentication to your admin accounts
Posted by: admin 10 years, 3 months ago
Seems like we just made the case for requiring two-factor authentication for Cisco Admins due to the SYNFul attack. Now here's another one.
SYNFUL attack shows the need for 2FA on routers
Posted by: admin 10 years, 3 months ago
Cisco has confirmed that the SYNFUL attacks discovered byFireEye are not the result of a vulnerability but rather:
Defense at every stage
Posted by: admin 10 years, 5 months ago
Another tweet struck me for it's common sense and truth:
The two things that actually work in information security and how to deploy them.
Posted by: admin 10 years, 7 months ago
I was struck by this tweet by @chrisrollf: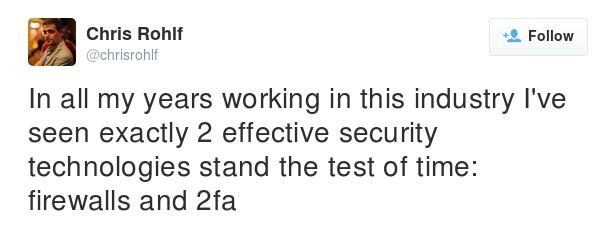
Recent Posts
- Blast-RADIUS attack
- The latest WiKID version includes an SBOM
- WiKID 6 is released!
- Log4j CVE-2021-44228
- Questions about 2FA for AD admins
Archive
2024
2022
- December (1)
2021
2019
2018
2017
2016
2015
2014
- December (2)
- November (3)
- October (3)
- September (5)
- August (4)
- July (5)
- June (5)
- May (2)
- April (2)
- March (2)
- February (3)
- January (1)
2013
2012
- December (1)
- November (1)
- October (5)
- September (1)
- August (1)
- June (2)
- May (2)
- April (1)
- March (2)
- February (3)
- January (1)
2011
2010
- December (2)
- November (3)
- October (3)
- September (4)
- August (1)
- July (1)
- June (3)
- May (3)
- April (1)
- March (1)
- February (6)
- January (3)
2009
- December (4)
- November (1)
- October (3)
- September (3)
- August (2)
- July (5)
- June (6)
- May (8)
- April (7)
- March (6)
- February (4)
- January (427)
2008
- December (1)
Categories
- PCI-DSS (2)
- Two-factor authentication (3)
Tags
- wireless-cellular-mobile-devices (7)
- Two-factor authentication (10)
- Wireless, cellular, mobile devices (6)
- NPS (1)
- Phishing and Fraud (111)
- Active Directory (1)
- pam-radius (3)
- privileged access (2)
- Cloud Security (10)
- Mutual Authentication (60)
- Web Application Authentication (1)
- Authentication Attacks (99)
- pci (50)
- Security and Economics (97)
- WiKID (133)
- pam (2)
- VPN (1)
- Installation (2)
- RADIUS Server (1)
- Open Source (64)
- Tutorial (2)
- Strong Authentication (35)
- Information Security (137)
- Transaction Authentication (13)
- Miscellaneous (100)
- Linux (2)
- transaction-authentication (6)
- Two Factor Authentication (254)
