Posted by:
admin
11 years, 8 months ago
The 2014 Verizon DBIR once again points to the need for two-factor authentication, just like last year. Hackers continue to use lost, stolen or weak credentials in attacks - three-quarters of all attacks. Imagine implementing a control that impacted 3/4ths of all attacks? Would that be beneficial. You bet.
But the data provides even more guidance. The vast majority of attacks are from the outside:
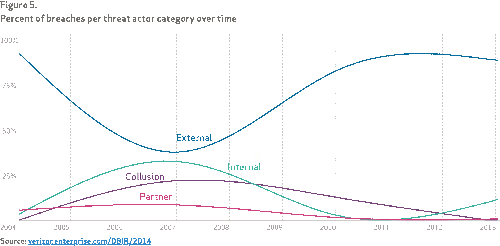
Therefore, locking down remote access with two-factor authentication is a must. The DBIR's recommendations such as use anti-virus, disable Java in the browser, patching etc. point to implementing NAC as well. We recommend using RADIUS and configuring it so users can be easily disabled. Configure the NPS RADIUS plugin to perform authorization based on the AD username in AD and then proxy the authentication to your two-factor auth server. Note that the users login with their AD username and OTP, not their AD passwords.
Attackers may still get in perhaps through vulnerable software. The next step is to harden their targets, which are increasingly your servers where the critical data is stored:
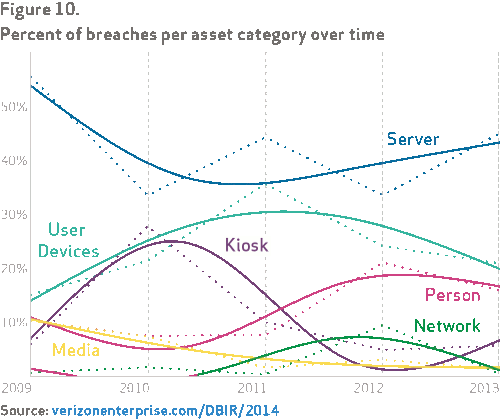
Time to start segmenting your servers and locking them down as if your admins are coming in remotely. If you are under PCI, you're doing this already for your in scope servers. It might be time to expand that policy. If you use pam-radius on Linux or either an SSL-VPN or RDP gateway on Windows (or many other possible mechanisms), you can use the same RADIUS setup for network segmentation that you do for remote access. Don't over-complicate things.
The DBIR continues to improve with age. Kudos to the team at Verizon!
Share on Twitter Share on FacebookRecent Posts
- Blast-RADIUS attack
- The latest WiKID version includes an SBOM
- WiKID 6 is released!
- Log4j CVE-2021-44228
- Questions about 2FA for AD admins
Archive
2024
2022
- December (1)
2021
2019
2018
2017
2016
2015
2014
- December (2)
- November (3)
- October (3)
- September (5)
- August (4)
- July (5)
- June (5)
- May (2)
- April (2)
- March (2)
- February (3)
- January (1)
2013
2012
- December (1)
- November (1)
- October (5)
- September (1)
- August (1)
- June (2)
- May (2)
- April (1)
- March (2)
- February (3)
- January (1)
2011
2010
- December (2)
- November (3)
- October (3)
- September (4)
- August (1)
- July (1)
- June (3)
- May (3)
- April (1)
- March (1)
- February (6)
- January (3)
2009
- December (4)
- November (1)
- October (3)
- September (3)
- August (2)
- July (5)
- June (6)
- May (8)
- April (7)
- March (6)
- February (4)
- January (427)
2008
- December (1)
Categories
- PCI-DSS (2)
- Two-factor authentication (3)
Tags
- wireless-cellular-mobile-devices (7)
- Two-factor authentication (10)
- Wireless, cellular, mobile devices (6)
- NPS (1)
- Phishing and Fraud (111)
- Active Directory (1)
- pam-radius (3)
- privileged access (2)
- Cloud Security (10)
- Mutual Authentication (60)
- Web Application Authentication (1)
- Authentication Attacks (99)
- pci (50)
- Security and Economics (97)
- WiKID (133)
- pam (2)
- VPN (1)
- Installation (2)
- RADIUS Server (1)
- Open Source (64)
- Tutorial (2)
- Strong Authentication (35)
- Information Security (137)
- Transaction Authentication (13)
- Miscellaneous (100)
- Linux (2)
- transaction-authentication (6)
- Two Factor Authentication (254)
