The Cisco ASA is a very popular VPN solution and the IP Sec VPN is probably it's most used feature. This document covers how to use radius to add two-factor authentication via WiKID to an ASA using the ASDM management interface. If you have not downloaded the WiKID Strong Authentication server, we recommend you start there. Once that is set up, you can configure the ASA to proxy authentication request directly to WIKID or through the MS Radius server NPS to WiKID. If you have questions about the network architecture, please see our eGuide on adding two-factor authentication to your network.
We assume you have your VPN substantially configured. We will start by adding a RADIUS server. We recommend using RADIUS as your protocol for a number of reasons - it is a good standard, works everywhere and can be configured to incorporate authorization via Active Directory or LDAP allowing simple user disablement.
Under Remote Access VPN select AAA/Local Users and click on AAA Server Group.
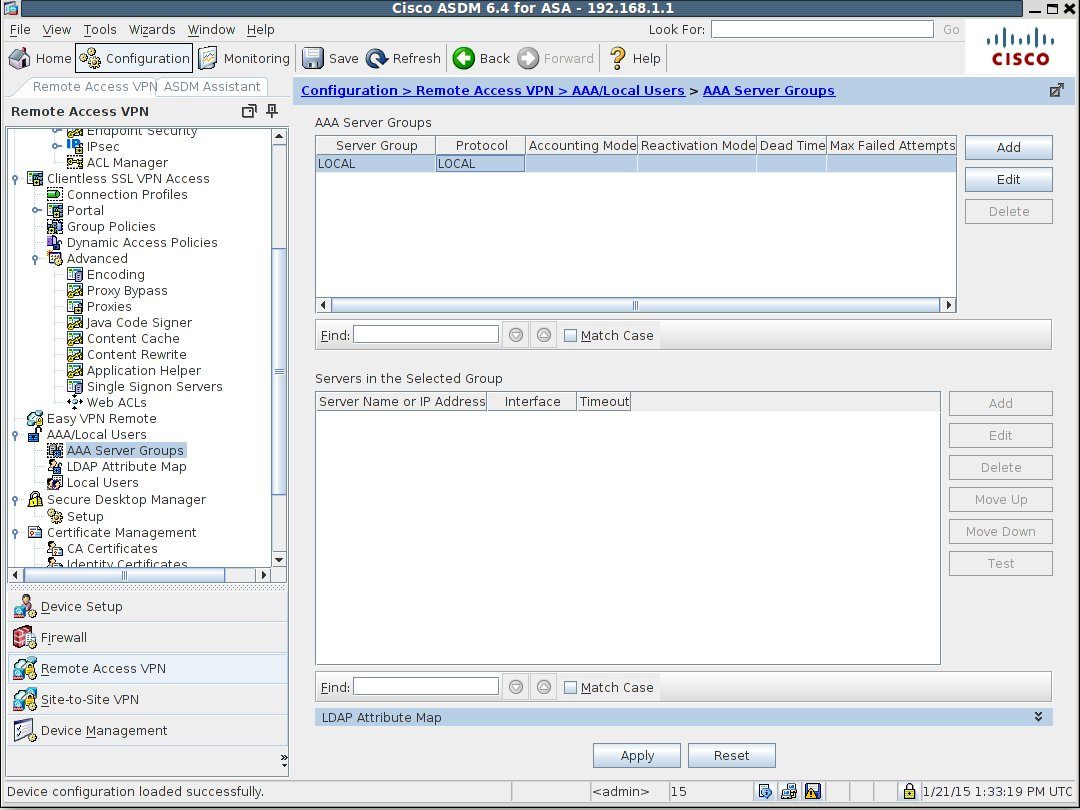
Click the Add button to add a server group.
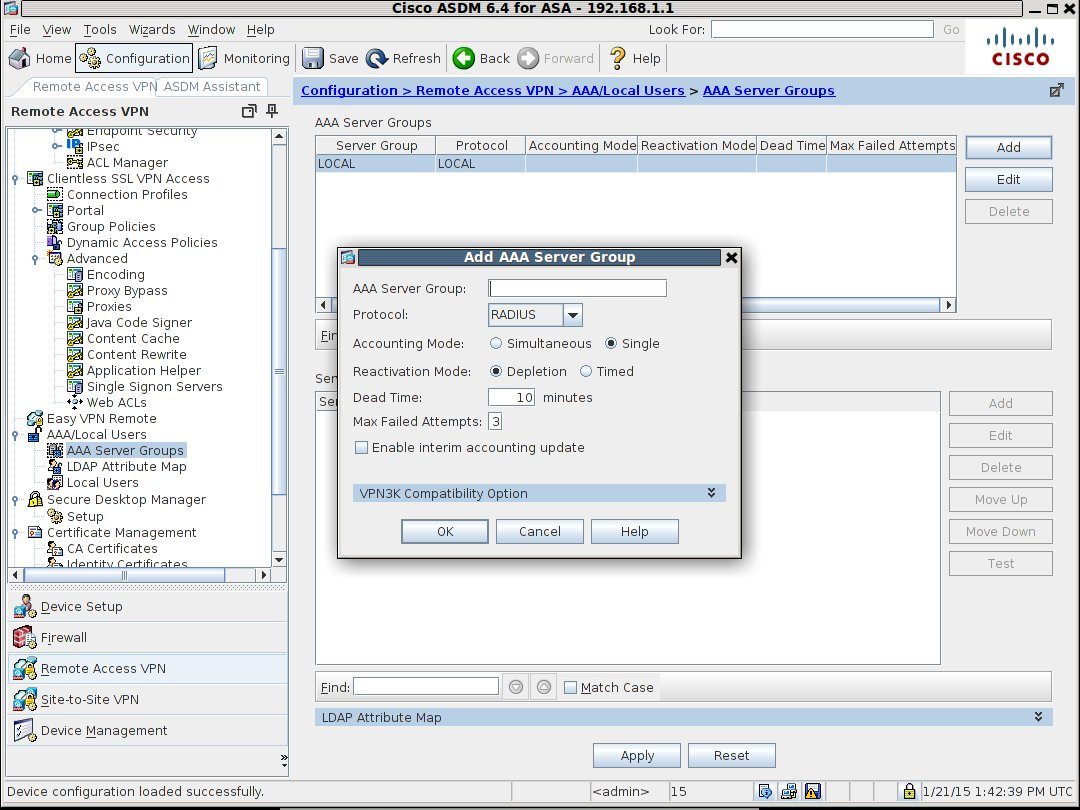
Give the server group a useful name such as "Two-factor-Auth" or "WiKID-RADIUS". No spaces are allowed. Hit OK.
Now, you will see that you can Add a server in the bottom panel under 'Servers in the Selected Group'. Do so.
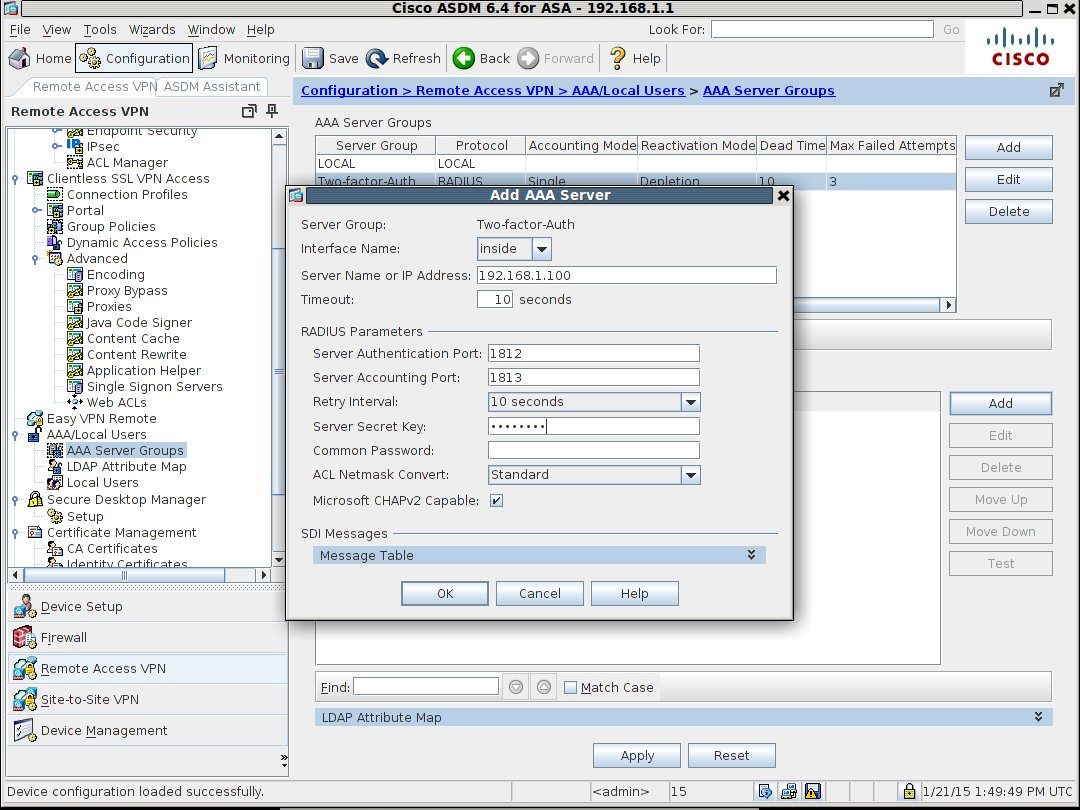
Specify the interface and IP address of either your RADIUS server - NPS if you are trying in Active Directory or the WiKID server if you are not. Again, we recommend tying in authorization by AD as a user would only need to be disabled in AD to be locked out completely.
Under RADIUS Parameters, change the Server Authentication Port to 1812. (The standard changed from 1645 in 2000 so it's completely understandable that Cisco hasn't updated yet. Clearly they have put all their money into updating the ASDM.). Set the Accounting port to 1813 and create or enter a Server Secret Key. This is the shared secret that will need to be the same on your RADIUS server. Remember RADIUS is encoded - not encrypted, so no RADIUS over the open Internet! Hit OK. And the Apply.
Next, click on Network (Client) Access and IPsec(IKEv1) Connection Profile
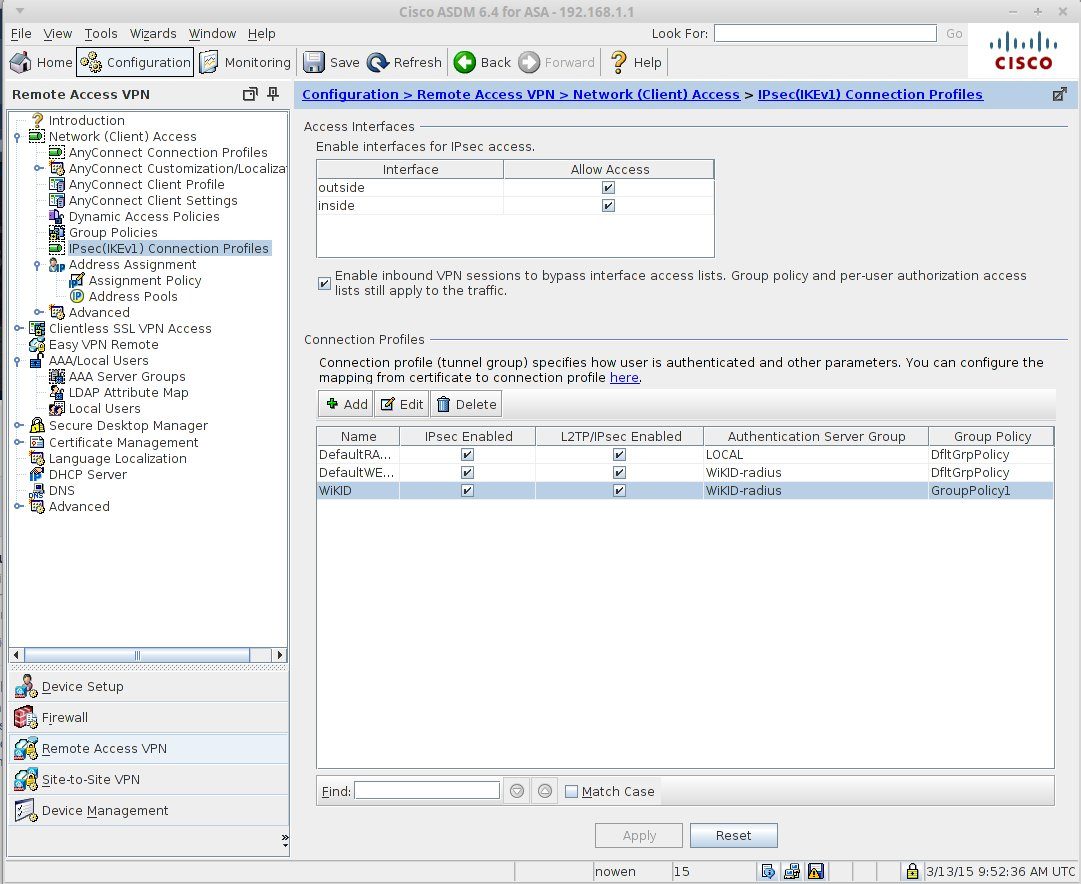
Click Add (or edit). Enter the appropriate information, choosing the Radius server group you created above.
That's it. The ASA is ready for two-factor authentication. At this point if you are using NPS, you should configure NPS for two-factor authentication. We recommend you first test the ASA/NPS connection using AD passwords and then add the WiKID server as a radius server on NPS. Once that is complete, the users will login with their AD user name and the OTP. NPS will perform authorization based on the user name alone. No sense in requiring a password!
Next we will configure the WiKID server. If you have not downloaded the WiKID two-factor authentication server, do it now. It's free for up to five users. We assume you have it up and running, generating one-time passwords. We will start by adding a network client. This can either be your RADIUS server if you are using freeradius or NPS or the ASA itself if you want them talking directly. On the WiKIDAdmin click on the Network Clients tab.
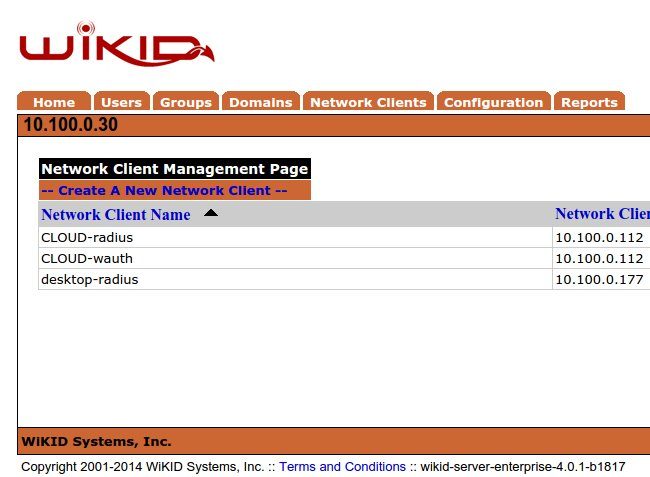
Click on Create a New Network Client.
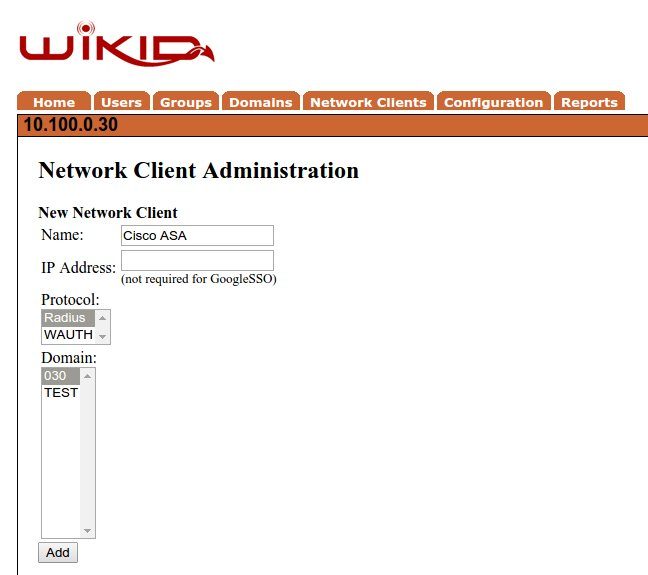
Give it a useful name, enter the IP address of the RADIUS server or the Cisco ASA depending on your setup. Select RADIUS as the protocol and select the WiKID domain to use. Click Add.
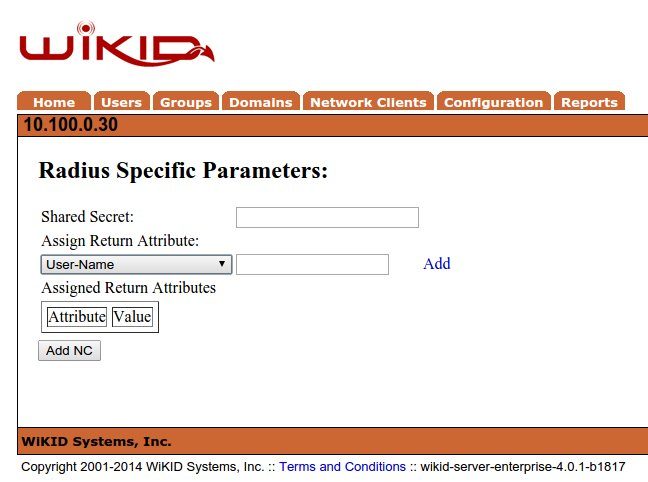
Enter the Shared secret. Remember this must match what is entered in the RADIUS server or the Cisco ASA or WiKID will not be able to decode the RADIUS packets.
On the WiKID terminal run 'wikidctl restart'. This updates the RADIUS cache and if you are using our ISO virtual appliance opens up the firewall for the IP address of the network client. If you are using the packages, please open port 1812 UDP for the correct IP address.
Now let's test it. Start your WiKID token and get an OTP for the WiKID domain you specified for the network client.
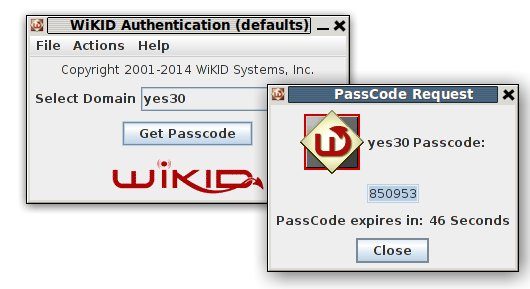
You can test the RADIUS authentication on the ASDM under AAA Server Group/Servers in the Selected group without having to login to the VPN from the outside.
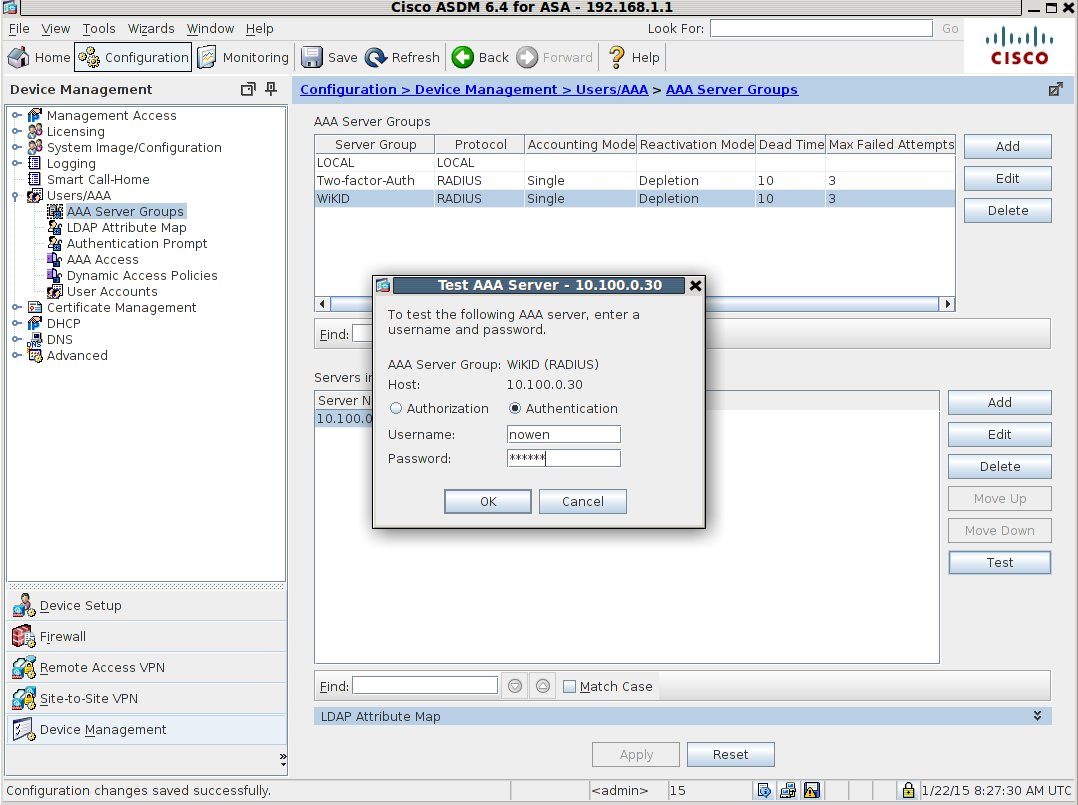
Hopefully, your test was successful:
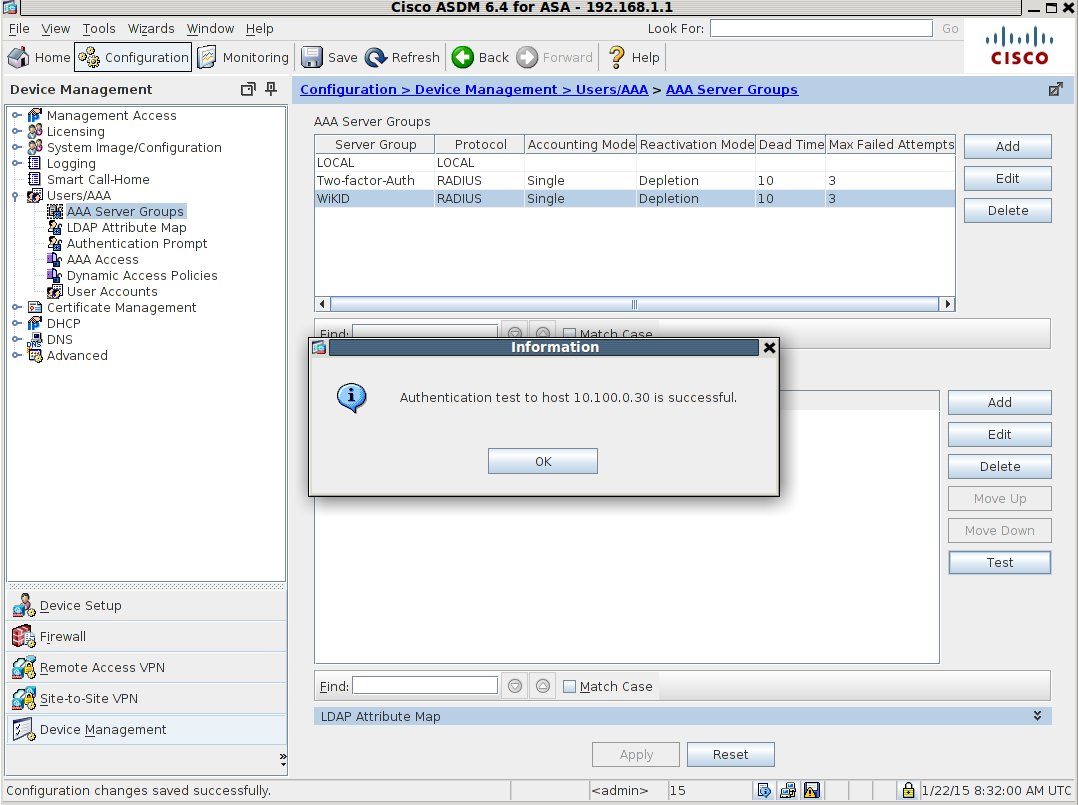
If not, please see these tips on trouble-shooting RADIUS.
(We also have a screencast for the Cisco 5500.)
Remember: we offer five free two-factor authentication licenses. Download the server today!
