Squid is a very useful piece of software. It can be used as a proxy to reduce outbound traffic requirements or in front of a set of webservers to increase overall system speed. In the words of the Squid web site:
Squid is used by hundreds of Internet Providers world-wide to provide their users with the best possible web access. Squid optimizes the data flow between client and server to improve performance and caches frequently-used content to save bandwidth. Squid can also route content requests to servers in a wide variety of ways to build cache server hierarchies which optimize network throughput.
In this guide we will show how Squid can be configured to support two-factor authentication from a WiKID server, allowing users to be centrally authenticated, but their requests still distributed for efficiency.
Configuring Squid
First, configure auth_param to use pam_squid:
auth_param basic program /usr/lib/squid/pam_auth
Then set the ACL rules:
acl pam proxy_auth REQUIRED http_access allow pam
You will need to delete the other http_access rules.
For testing, I configured a simple setup where Squid accelerated Apache on the same server:
visible_hostname your_hostname http_port external_IP:80 accel defaultsite=your_hostname cache_peer 127.0.0.1 parent 80 0 no-query originserver
At this point you should test your Squid configuration using a valid user account on the box as the default setup for pam with Squid is to use system-auth. It's always a good idea to start simple and test each new layer of complexity.
Configuring PAM for Squid
In this example, we will use Pam Radius to connect Squid with WiKID. There is excellent documentation on installing pam_radius at the PAM Radius home page. Depending on your distribution, you might also be able to find a suitable binary. I had no trouble compiling this on Fedora 7:
# ./configure # make # make install
Open the file in your favorite editor and edit /etc/pam.d/squid to allow Radius authentication:
Go to the second line of the file and insert this line:
auth sufficient /lib/security/pam_radius_auth.so
just above this line:
auth required pam_stack.so service=system-auth
The "sufficient" tag indicates that if the Radius authentication succeeds then no additional authentication will be required. However, if the Radius authentication fails, a username and password from the system will work. Use "Required" to require strong authentication. Because we are only editing the sshd file, it will not affect terminal log-ins. PAM can be very different on different linux variants. Consult the specific documentation for your OS.
Edit or create your /etc/raddb/server file:
Assuming that the users won't have have local accounts on your Squid server, you can comment out those lines and add in lines for radius:
#%PAM-1.0 #auth include system-auth auth required /lib/security/pam_radius_auth.so #account include system-auth account include /lib/security/pam_radius_auth.so
Configuring the WiKID Server
Now, we'll configure the WiKID server to process the one-time passwords from Squid. Additional WiKID installation documentation is available here.
Log into the WiKID server using the WiKIDAdmin browser interface and click on the Domains Tab (If you already have a domain setup, you can skip this step.)
Click on Create a New Domain,
Enter the information requested. The Domain Server code is the zero-padded IP address of the WiKID server. So, if the external IP address is 216.239.51.99, the WiKID server code would be 216239051099. Click "Create".
Click Network Clients tab and on "Create a new Network Client".
Enter the information requested. For the IP Address, use the IP address of the Squid server. Select Radius and the domain you just created. Click "Add" when you're finished.
On the next page, enter the shared secret you entered in /etc/raddb/server. You do not have to enter any information under "Return Attributes".
Important: From the WiKID server's console or via SSH, you will need to run "wikidctl restart" to load the new configuration into the WiKID Radius server. (WiKID 2.0 users just run "stop" and "start".)
Testing Squid access with one-time passwords
Download and install a WiKID Token client. You can manually validate yourself as a user from the WiKIDAdmin web interface. Once validated, select the Domain associated with Squid:
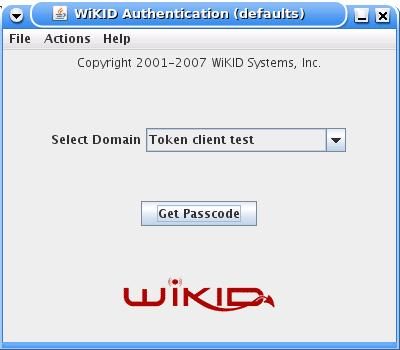
Enter the PIN:
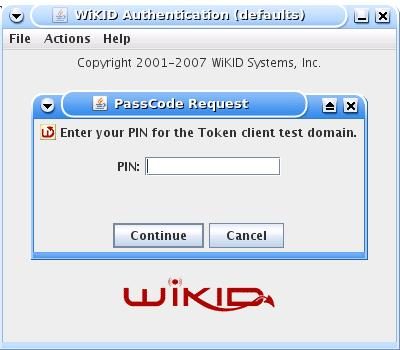
And you will get back the one-time passcode. The OTP is time-bounded, but the time can be set on the WiKID server to whatever you want:
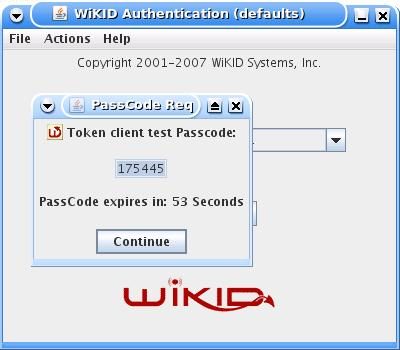
Now browse to the Squid URL. You should get the typical http login window. Log in with your username and WiKID one-time passcode and you're done! If you have any problems, you can check your squid logs (/var/log/squid/access.log on Fedora) and the WiKID logs via the WiKIDAdmin web interface or at /opt/WiKID/logs/radius.log.
Conclusion
Squid is a very powerful tool, useful for accelerating inbound and outbound access. Often, Squid is used to dispatch different requests to different web application machines. Letting Squid handle the authentication allows centralized control of the user database which reduces complexity. Combine that with two-factor authentication and you have security and simple maintenance.
This article was originally published on Howtoforge
