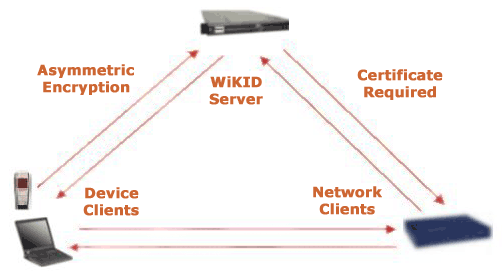
Fundamentally, WiKID Strong Authentication works this way: A user selects the domain they wish to use and enters the PIN into their WiKID Two-factor client. It is encrypted with the WiKID Server's public key - assuring that only that server can decrypt it with its private key. If the server can decrypt the PIN and it is correct and the account is active, it generates the one-time passcode (OTP) and encrypts it with the client's public key. The user then enters their username and the OTP into whatever service they are using, a VPN e.g., which forwards it to the WiKID Server for validation.
The subsequent pages address each segment of the WiKID architecture: Domains, Token Clients, Network clients and protocols. Additional information on transaction and mutual https authentication follows.
